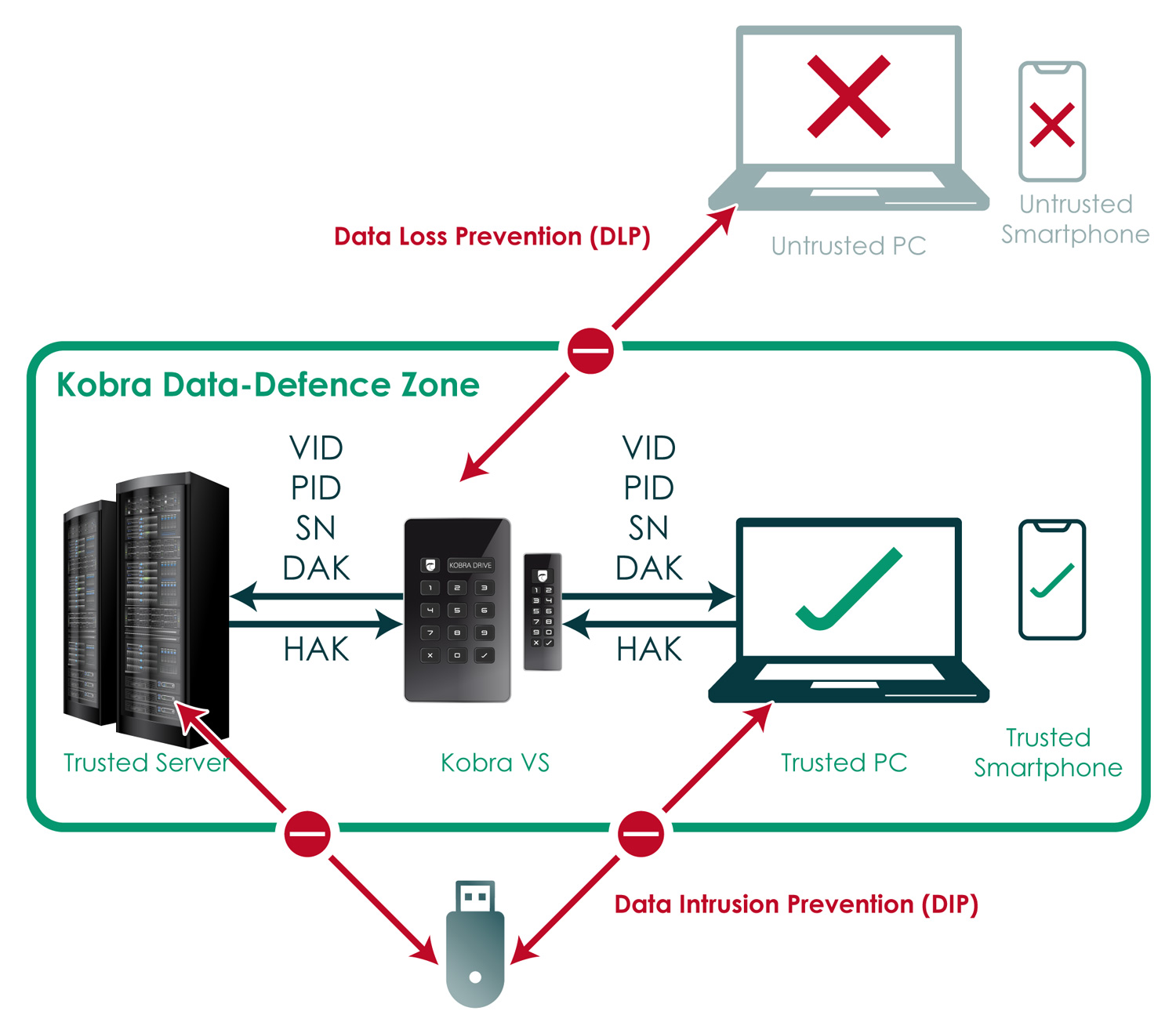
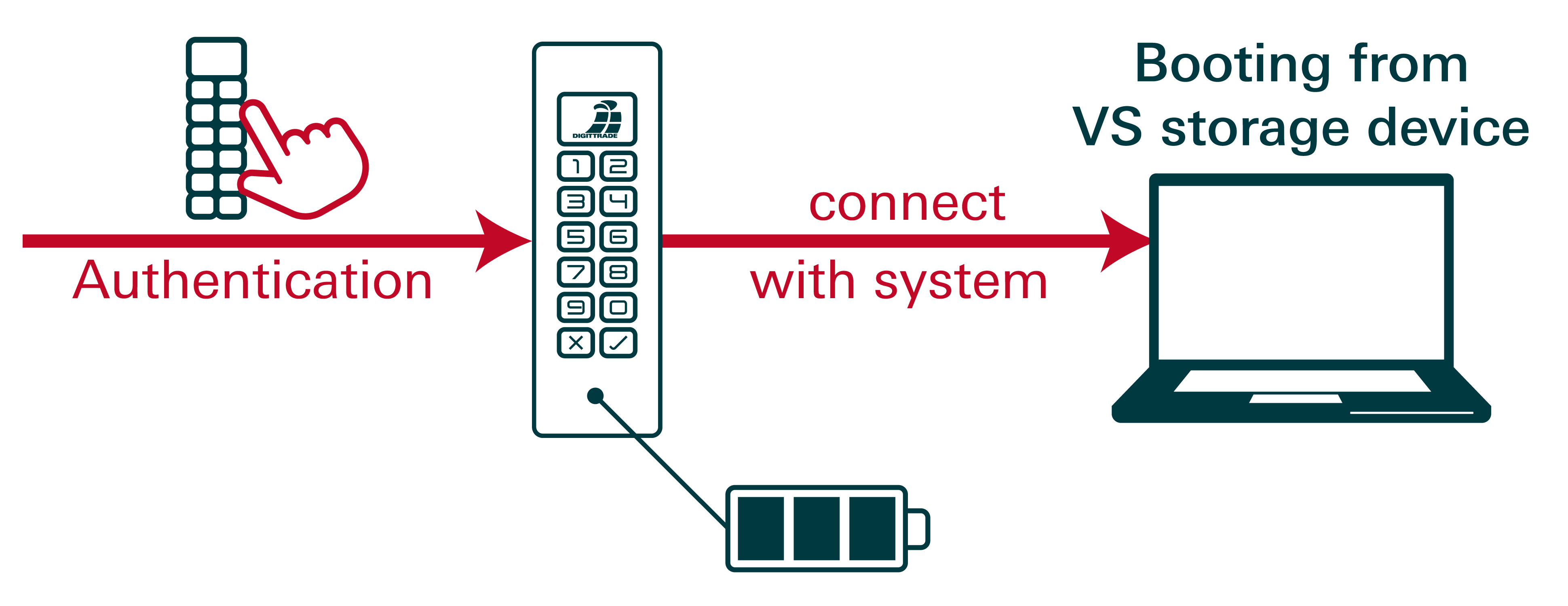
The features of the Kobra VS storage devices (Kobra Stick VS and Kobra Drive VS) offer extensive possibilities for the secure storage, archiving and transmission of sensitive, personal and confidential information up to classification level EU RESTRICTED, NATO RESTRICTED and German VS-NfD.
The following application scenarios are also within the scope of the German VS-NfD-, NATO-Restricted and EU-Restricted approval by the German Federal Office for Information Security (BSI). Deviations from the described procedures must be approved by the German Federal Office for Information Security (BSI).





Windows® is a registered trademark of Microsoft Corporation.
Kobra Infosec GmbH